
“Please respond ASAP.” When CFO Joe receives an email from CEO Taylor with this urgent subject line, he goes into high alert. The message is pressing. The email’s sender,... Read more »
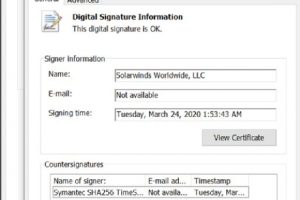
2020 was a roller coaster of major, world-shaking events. We all couldn’t wait for the year to end. But just as the 2020 was about to close, it pulled... Read more »
The majority of malware infections begin with a phishing email. These simple lures, which trick recipients into opening malicious attachments or clicking links that lead to malicious web content,... Read more »
Forensics teams are still investigating how hackers were able to exploit SolarWinds’ patching system to attack numerous high-profile commercial and governmental organizations, including Microsoft and the U.S. Department of... Read more »
Ransomware attacks are expected to grow both in frequency and effectiveness in 2021, with researchers at Cybersecurity Ventures predicting attacks to occur every 11 seconds and ultimately cost victims... Read more »

Modern security strategies should take an inside-out approach, not outside-in. “Understanding how to protect assets inside the security perimeter is far more important than focusing on preventing attackers from... Read more »
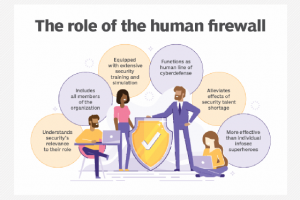
The proliferation of cybersecurity breaches is forcing government and business leaders to analyze the limitations of technology and reevaluate the role of people. Despite incredible advances in both threat... Read more »
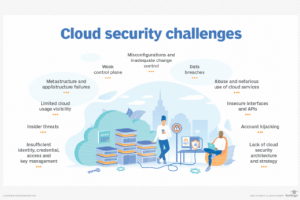
All the major promises of the cloud — improved IT efficiency, flexibility and scalability — come with one major challenge: security. Many organizations can’t delineate where cloud service provider... Read more »

One of the more popular cybersecurity trends in 2021 will undoubtedly be Secure Access Service Edge, or SASE. As enterprise networks evolve to better manage traffic from remote employees,... Read more »
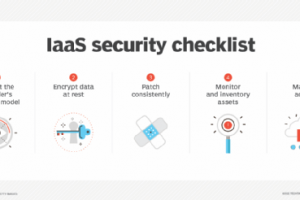
Many organizations have almost completely replaced virtual data centers, on-premises servers and appliances with IaaS. This widespread implementation requires a mobilization to secure IaaS environments to match this increased... Read more »

