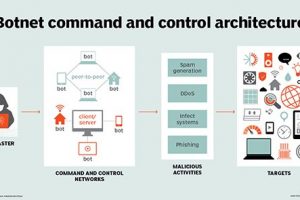
Although the terms security threat, security event and security incident are related, in the world of cybersecurity these information security threats have different meanings. A security threat is a... Read more »
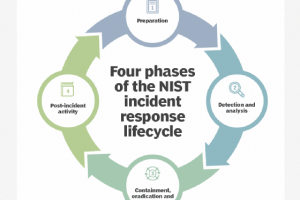
CERT, CSIRT, CIRT and SOC are terms you’ll hear in the realm of incident response. In a nutshell, the first three are often used synonymously to describe teams focused... Read more »

Be careful where you click. Ransomware, like other varieties of malware, is commonly distributed via phishing emails. One wrong click on a malicious link or attachment can result in... Read more »

Ransomware attacks constituted 81% of financially motivated cyber attacks in 2020 and cost more in damages than any other malicious attack, according to a report from Atlas VPN. As... Read more »

A key fact to know about network penetration testing for beginners: If an organization pays someone to try to break into its network, it typically wants that person to... Read more »

The saying, “If it isn’t broken, don’t fix it,” doesn’t necessarily line up with the idea of network penetration testing, where a tester breaks into something typically to fix... Read more »
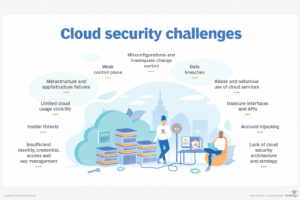
Organizations of all sizes have adopted cloud strategies to varying degrees. While beneficial in many ways, the cloud also has its risks, which organizations should fully assess before placing... Read more »

The average time to detect and contain a data breach is 280 days, according to IBM’s “2020 Cost of a Data Breach Report.” This makes clear that monitoring IT... Read more »
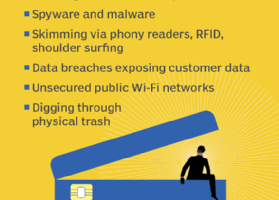
Given the exponential growth of e-commerce and online transactions, cybersecurity has never been more critical. Hackers may attempt to invade our privacy in several ways, but one area they... Read more »
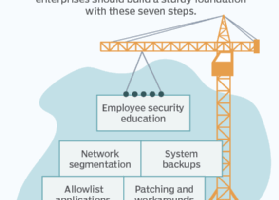
Without a strong network security strategy, IT security will fall short — and vice versa. The National Security Agency (NSA) has identified three basic functions to form the foundation... Read more »

