
Consumer users of McAfee’s antivirus products who found their service contracts auto-renewed for another year will now be able to end their contracts and obtain a refund for the... Read more »
In the past year, it would be eminently fair to say that the focus of the cyber security industry has not necessarily been on compliance with the General Data... Read more »
Cyber attacks exploiting vulnerabilities in unpatched legacy systems, via consumer applications such as TikTok, and originating from friendly countries may be a bigger risk to the average organisation than... Read more »
A cyber attack on the systems of airline IT services specialist Sita, first reported earlier in 2021, has claimed another victim in the aviation sector, after Air India revealed... Read more »

Dutch research institute TNO, in collaboration with various partners, has developed self-healing security software. This software is based on the functioning of the human immune system, based on the... Read more »
With a strategic five-year plan, Bureau Veritas (BV) set out on its digital transformation project in 2015. Core to that transformation was migration of the vast bulk of its... Read more »

MEPs have urged the European Commission (EC) to revise its draft decision to provide data adequacy to the UK to ensure that citizens in the European Union (EU) have... Read more »
In this episode of the Computer Weekly Downtime Upload podcast, Caroline Donnelly and Brian McKenna are joined by Alex Scroxton, security editor, to discuss the recent CyberUK conference, bees... Read more »

The discovery of 23 leaky Android applications by Check Point Research (CPR) – which may, collectively, have put the personal data of more than 100 million users at risk... Read more »
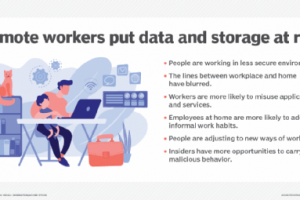
Considering the dramatic increase in remote access to IT resources during the COVID-19 pandemic, management of remote access security has become an essential activity. Organizations should establish policies and... Read more »

