
New Zealand’s serving privacy commissioner John Edwards has been selected by the UK government as the preferred candidate to succeed Elizabeth Denham as information commissioner when she steps down... Read more »

Almost half (45%) of cyber security professionals believe that calling in law enforcement following a ransomware attack slows down the recovery process and distracts the victim’s IT and security... Read more »

Individuals and organisations in the UK reported losses of £1.3bn to fraud and cyber crime between 1 January and 31 July 2021, a threefold increase on the year-ago figure... Read more »

Linux-based operating systems are being targeted more and more frequently by malicious actors, largely thanks to the prevalence of Linux in public cloud workloads. More than 13 million attempted... Read more »

Up to and possibly more than 50% of Microsoft Exchange servers located in the UK appear to be vulnerable to three distinct vulnerabilities that were patched some time ago,... Read more »

With a global surge in ransomware attacks, governments have concentrated their attention on what drives these attacks’ popularity among cyber criminals. Most have concluded that it is their profitability.... Read more »

A public backlash against NHS Digital’s General Practice Data for Planning and Research (GPDPR) data-sharing plan saw more than a million people exercise their right to opt out of... Read more »

Civil society groups have called for a ban on the use of life facial-recognition (LFR) technology amid claims that the government and the police are introducing intrusive surveillance measures... Read more »
Looking at log files generated by IT infrastructure software is one of the less exciting parts of an IT administrator’s job, but those log files determine the health of... Read more »
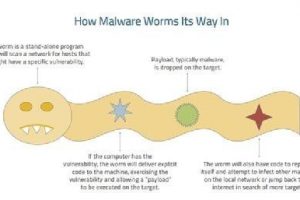
What is the ILOVEYOU virus? The ILOVEYOU virus comes in an email with “ILOVEYOU” in the subject line and contains an attachment that, when opened, results in the message... Read more »

