While the cloud is playing an increasingly pivotal role in the modern business world, companies migrating to remote infrastructure face a host of challenges — and arguably chief among them is the issue of security.
Hosting applications and data in the cloud is a reality for countless companies today. But knowing exactly what’s going on under the hood isn’t always easy due to the complexity of integrations at play spanning everything from API gateways to Kubernetes. The upshot is that identifying security policy violations can get a little tricky.
This is a problem that Paladin Cloud is setting out to solve, with an open source “security-as-code” platform that launches to the public today.
Paladin’s core raison d’être is to help developers and developer operations (DevOps) teams safeguard their applications and data, both in testing and production environments — and it does so by serving full visibility into the security posture of their myriad cloud services and enterprise systems. Ultimately, it’s all about automating the detection and remediation of security policy violations, which may include anything from unauthorized access or misconfigurations, to insecure APIs.
To help take the open source project to the next stage and further toward commercialization, the Piscataway, New Jersey-based startup today announced it had raised $3.3 million in a seed funding round co-led by Okapi Venture Capital and Bowery Capital, with participation from a slew of notable backers including Samsung Next, T-Mobile Ventures, SaaS Ventures, Touchdown Ventures, and UST.
Plugin architecture
Paladin adopts a plugin-based architecture that helps developers connect to and ingest data from myriad sources, spanning code repositories, threat intelligence systems, API gateways, Kubernetes, and more. Paladin can then discover all the assets, evaluate and establish policy violations, and execute any pre-configured auto-fixes.
While Paladin is designed to secure all the major public clouds including AWS, Azure, and Google Cloud, as an open source project, it’s flexible and extensible. This means that it can be used as part of companies’ hybrid cloud strategies, where some of their data and applications are hosted between public and private cloud infrastructure — Paladin can be used to build bridges between these disparate systems.
To get a better idea of the world in which Paladin has entered, there a number of other similar players in the space — these include Wiz, a $6 billion company; Bridgecrew, which was recently snapped up by Palo Alto Networks for $156 million; and Accurics, which was acquired by Tenable for roughly the same amount. Not to mention other fledgling startups such as Jit, which recently exited stealth with a chunky $38.5 million in seed funding.
So it’s clear there is real demand for cloud-native security in the age of DevOps. However, Paladin is pitching its open-source foundation as one of its core differentiators. The benefits are the usual advantages the open source solutions bring to the table, including the fact that open source is an incredibly attractive proposition to developers who prefer to tinker with and test-drive software themselves, without having to jump through giant corporate hoops.
“Developers prefer to deploy open source solutions versus closed source,” Paladin cofounder and CEO Daniel Deeney told TechCrunch. “To date, closed source players sell their products to CISO or security teams as paid enterprise solutions. Many developers do not use these products because they don’t have a budget oftentimes to purchase expensive enterprise solutions, and these products are not flexible to integrate into other cloud based systems.”
While there are other open source players in the space (including venture-backed Stacklet), Paladin is touting its “holistic approach” to cloud security which includes the aforementioned connector-based architecture that extends security not only across the major public clouds, but an extensive gamut of cloud technologies such as Kubernetes.
The story so far
Paladin has existed in stealth mode as a self-funded project since the tail-end of 2021, and in the intervening months the founders — Deeney and CTO Steve Hull — have been building out the product in conjunction with partner customers and developers from the community.
Today’s announcement heralds the official launch of the core Paladin open source project on GitHub, which includes a bunch of features out-of-the-box including a UI management dashboard; best-practice security policies spanning the major clouds; a policy-management plane to connect directly into cloud-based enterprise systems; role-based access control (RBAC); severity-based prioritization of policy violations; and more.
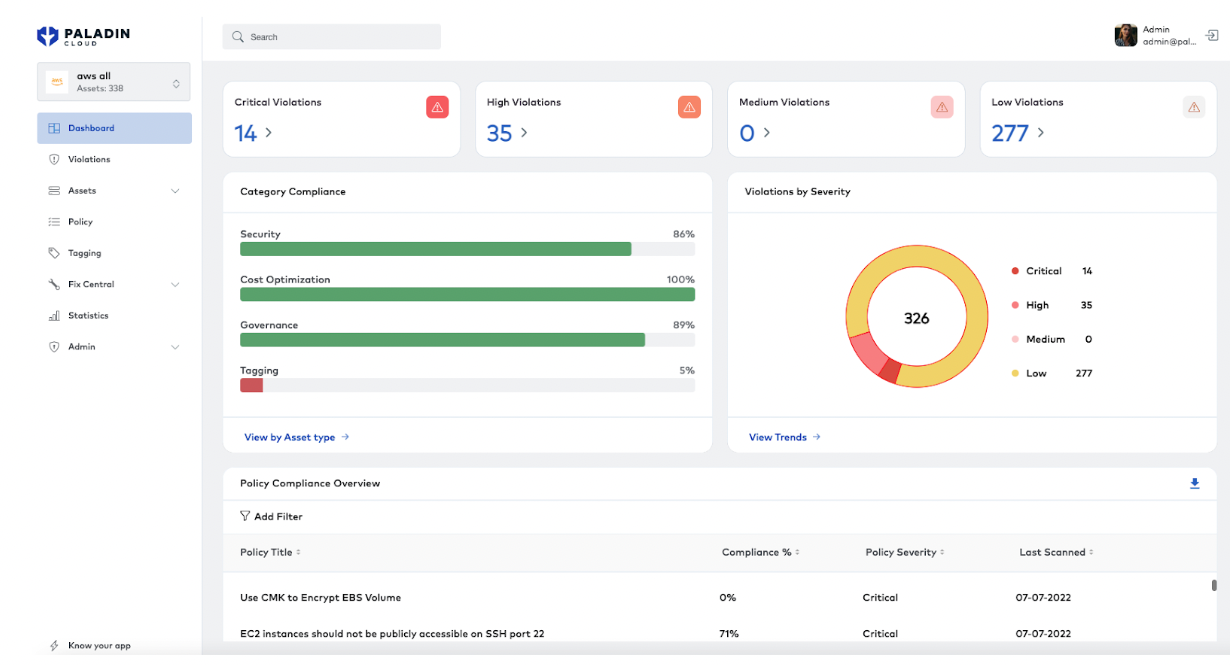
Paladin dashboard
This also signals the beginning of what will eventually be a fully commercialized product. This will include an enterprise-grade offering with self-service SaaS platform, and premium features such as service level agreements (SLAs), AI-based risk-scoring, and enhanced compliance reporting.
Paladin says that it is already providing commercial support to at least one publicly-traded enterprise.
“In addition to many developers using the beta version of the OSS (open source software) product, Paladin has signed a multi-year OSS support contract with a public company based in Philadelphia to launch the open source product,” Deeney said. “Due to a confidentiality agreement, the company is not allowed to disclose the customer name right now.”
But before the big monetization push, Paladin is now well-financed to fund its growth in the open source community by building out its team.
“The company is planning to use the seed round proceeds to hire a few key positions, such as head of developer relations, and to build up its development team,” Deeney said.

